You’ve probably used a digital signature without giving it much thought: signing a contract, verifying a website, or sending a secure email. But behind that smooth experience is a quiet powerhouse making it all happen: PKI.
Let’s break it down: no tech terms, no textbook terms. Just what you need to know about Public Key Infrastructure (PKI), why it’s critical to security, and how digital signatures have evolved into a trust-building must-have for any modern business.
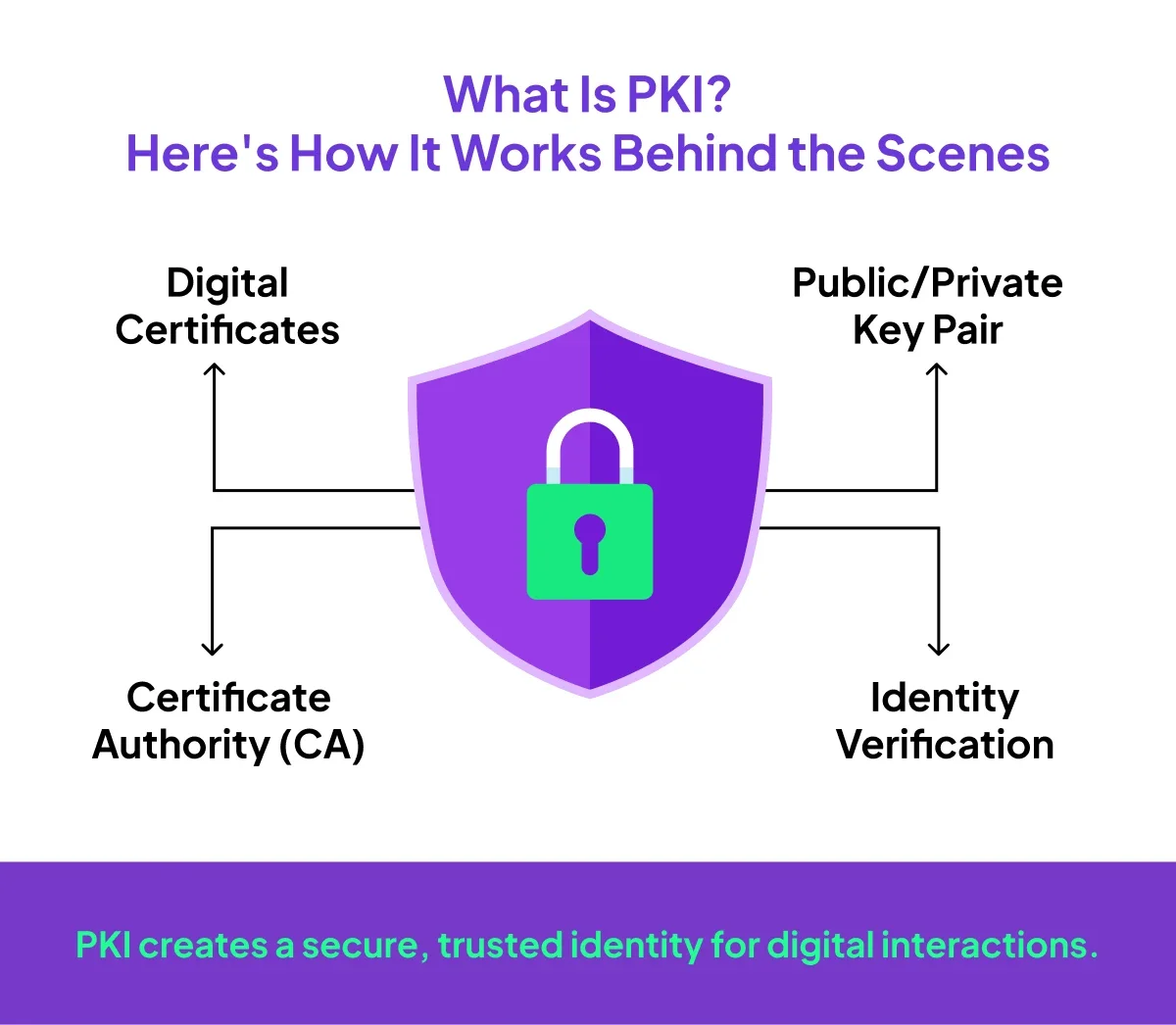
What Is PKI Exactly?
At its core, PKI is a framework that helps people and systems verify each other’s identity online. It does this using a combination of digital certificates and encryption — a fancy way of saying “we make sure the person you’re dealing with is real, and that the data hasn’t been messed with.”
Here’s a simple way to think about it:
- A digital certificate = your online ID card
- A Certificate Authority (CA) = the trusted body that gives you that ID
- Your private key = the thing only you have access to
- Your public key = the one you share with others
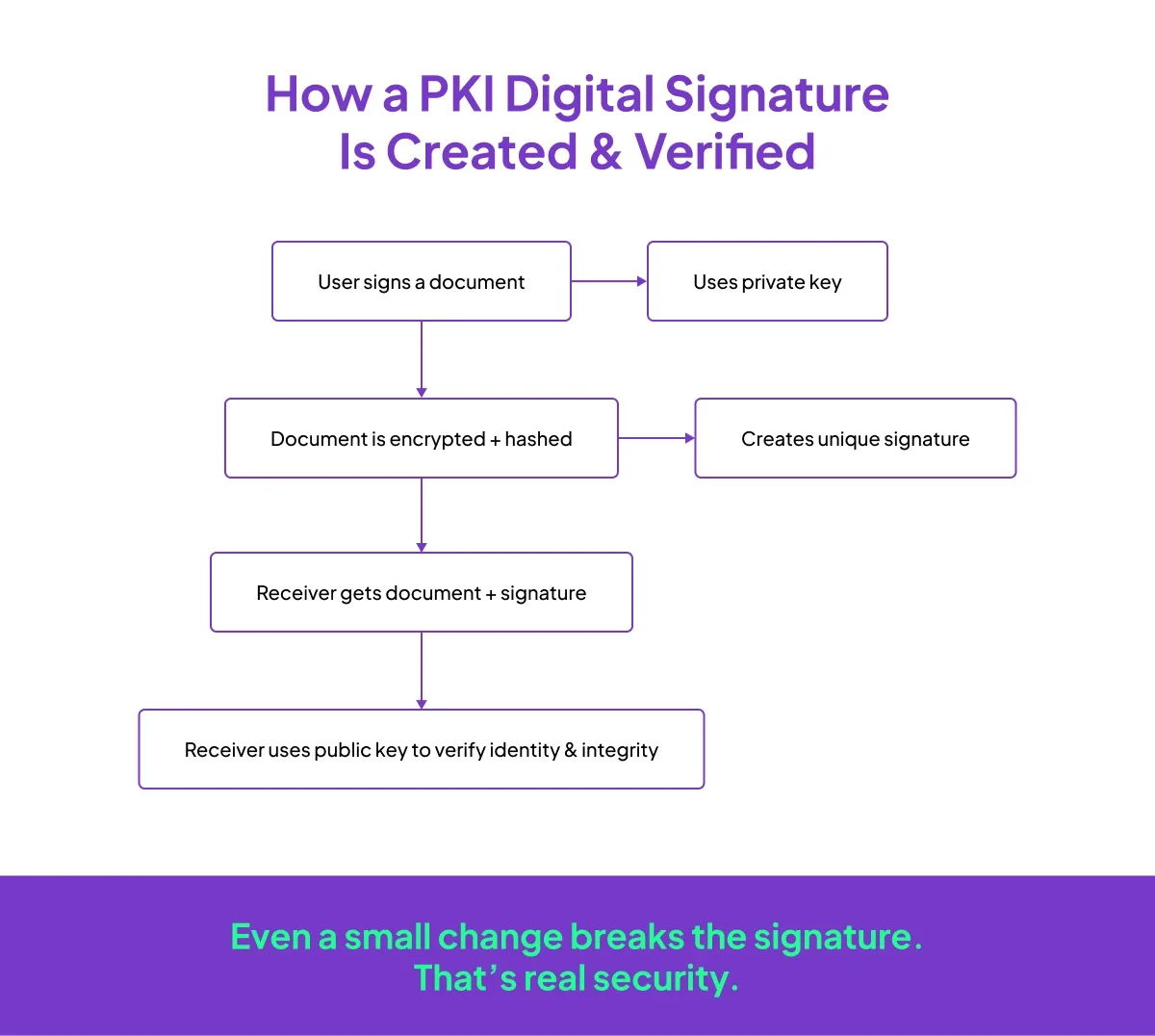
When you sign something digitally using PKI, it’s like locking the document with your private key. Only your matching public key can unlock and verify that signature. If the document is tampered with? The signature immediately fails.
Digital Signatures: More Than Just “E-Signing”
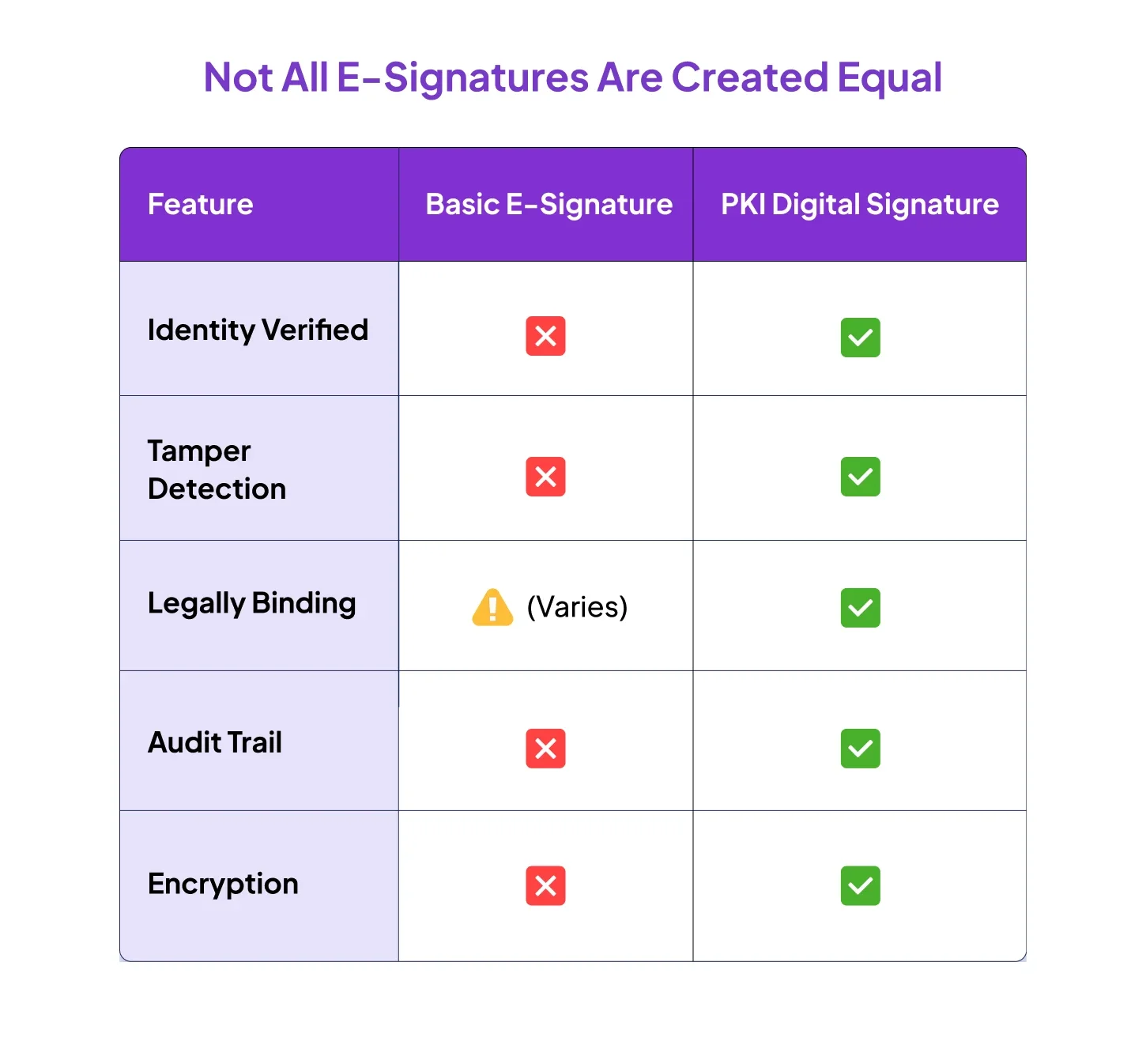
There’s a big difference between clicking “I agree” on a pop-up and a PKI-based digital signature.
With PKI:
- You’re proving your identity with a verified certificate
- Your signature can’t be forged
- The document is locked from tampering
- A timestamp and audit trail are automatically created
So, if someone tries to hack in a change after you've signed — even just a single character — the signature breaks, and the system flags it.
That’s why PKI-backed digital signatures are recognized under laws like India’s IT Act, the EU’s eIDAS, and others. It’s not just secure; it’s legally valid.
Why More Businesses Are Adopting PKI
Digital transformation isn’t just about going paperless — it’s about creating a system that is secure, reliable, and built for scale. That’s why more and more businesses, from fast-growing startups to established enterprises, are turning to Public Key Infrastructure (PKI) as the backbone of their document workflows and digital communications.
Here’s what makes PKI such a compelling choice:
1.Verified Identity
In a world where emails can be spoofed, logins can be compromised, and even signatures can be faked, knowing who you’re dealing with has never been more important.
PKI-based digital signatures tie every action — whether it’s signing a contract or accessing a platform — to a verified digital certificate. This certificate is issued only after the identity of the person or system is authenticated by a trusted authority. So, when you receive a signed document, you’re not just guessing it came from the right person — you know it.
This eliminates impersonation risks, builds trust between parties, and is especially critical in industries where decisions carry high financial, legal, or reputational stakes.
2.Document Integrity
You send a signed agreement to a client. They review it, sign, and send it back.
But what if someone, somewhere, made a small change to the document before finalizing it?
With PKI, that kind of tampering is instantly exposed.
Every time a document is digitally signed using PKI, a unique fingerprint (technically, a cryptographic hash) of the document is locked in with the signature. If anyone tries to edit even a single character after signing, the system will know — and the signature will break.
This level of integrity is why legal teams, auditors, and compliance officers rely on PKI: it preserves the original version of a document with mathematical certainty.
3.Legal Protection
Not all electronic signatures are created equal. A checkbox or typed name may be fine for low-risk agreements — but they rarely hold up in court if challenged.
PKI-backed digital signatures are legally enforceable in many parts of the world, including under India’s IT Act, the European Union’s eIDAS regulation, and the U.S. ESIGN Act when combined with identity verification.
Why? Because a PKI signature provides:
- Verified signer identity
- Evidence of intent to sign
- Proof that the document has not been changed post-signature
- A timestamp and audit trail
This means your contracts aren’t just signed — they’re protected by a robust legal framework that can stand up to scrutiny.
Read: Discharge of Contract: Meaning and Types
Scalable Security
When you're small, managing signatures and approvals manually might work. But what happens when your team grows? Or when you need to sign and track dozens of contracts each day across departments, partners, or regions?
PKI is designed for scale.
It supports everything from one-off document signings to enterprise-wide encryption, onboarding, and access management.
You can issue digital certificates to hundreds (or thousands) of users, automate signing workflows, and integrate secure authentication into your existing systems — without sacrificing performance or control. Whether you're closing five deals a month or five hundred, PKI adapts to your growth without skipping a beat.
Centralized Control
Security isn't just about keeping the wrong people out — it's also about knowing who has access, when, and why.
With PKI, organizations can centrally manage digital certificates and signing privileges:
- Define who can sign, and at what level of authority
- Set certificate expiry dates and auto-renewals
- Revoke certificates instantly if an employee leaves or a key is compromised
- Maintain a full audit trail of every action
This level of oversight helps reduce the risks of unauthorized access or untraceable changes and simplifies compliance with internal policies and industry regulations.
For IT and security teams, it means fewer gaps and more visibility. For leadership, it means better control over critical decisions and approvals. And for employees, it’s a secure system that runs quietly in the background — without slowing them down.
How ZoopSign Helps You with PKI?
Let’s say you're part of a mid-sized enterprise closing a strategic partnership.
There are contracts to sign, multiple stakeholders involved, and the clock is ticking.
In the past, this might’ve meant:
- Dozens of email threads
- Printing, signing, scanning
- Delays because one person was out of the office
Now, enter ZoopSign’s Deal Room — a secure digital space where:
- All parties collaborate in one place
- Permissions control who can view, edit, or sign
- A PKI-based digital signature protects every document
- Activity logs track exactly who did what and when
The experience? Seamless.
The security? Iron-clad.
The deal? Closed — days faster than before.
That’s the power of wrapping PKI into user-friendly tools. You don’t need to understand encryption algorithms — you just need a reliable way to sign, share, and secure your most important documents.
Conclusion
You don’t have to memorize what PKI stands for (Public Key Infrastructure if you must). But knowing what it does? That’s business gold.
It helps you prove who you are. Protect what matters. And close deals without second-guessing the signature on the dotted line.
So whether you’re rolling out contracts, building secure workflows, or simply trying to future-proof your business, remember: a good PKI system is like Wi-Fi—you don’t always see it, but you absolutely need it.
And if you want to keep it simple, scalable, and secure? Let ZoopSign handle the heavy lifting.
FAQs
1. Is a digital signature the same as an e-signature?
Not quite. An e-signature could be anything from a scanned image to a checkbox. A PKI-based digital signature is cryptographically secure, tied to your identity, and legally enforceable.
2. Is PKI not suited for small businesses?
Not at all. If you’re dealing with sensitive documents, contracts, or regulated industries, PKI gives you peace of mind — no matter the size of your team.
3. What happens if someone’s certificate is compromised?
It can be revoked. PKI systems include Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) checks to ensure outdated or compromised keys are flagged.
4. Can I implement PKI on my own?
Technically yes, but it requires deep IT and security expertise. For most businesses, using a platform like ZoopSign that already integrates PKI under the hood is a faster, safer, and more scalable approach.